Implementing robust Microsoft 365 Defender phishing protection has become crucial for businesses of all sizes. With cyber threats evolving daily, organizations need a comprehensive security solution that can effectively guard against sophisticated phishing attempts and other malicious activities.
Understanding the Rising Threat of Phishing Attacks

Phishing attacks continue to be one of the most prevalent cybersecurity threats facing businesses today. Cybercriminals are becoming increasingly sophisticated in their approaches, creating convincing emails and websites that can fool even the most vigilant employees.
Common Phishing Tactics That Target Businesses
- Impersonation of executives and trusted sources
- Fraudulent payment requests
- Fake login pages for company resources
- Malicious email attachments
- Compromised business email accounts
How Microsoft 365 Defender Phishing Protection Works
The Microsoft 365 Defender phishing protection system operates through a multi-layered approach, combining advanced AI, machine learning, and real-time threat detection. This comprehensive security framework ensures that your organization stays protected against both known and emerging threats.
Key Security Features
1. Advanced Attachment Scanning
Every attachment that enters your system undergoes thorough scanning for potential threats. The system checks for malware definitions hourly, ensuring protection against the latest threats. Common high-risk file types like .exe, .app, and .scr are automatically blocked, providing an additional layer of security.
2. Intelligent Spam Filtering
The advanced anti-spam technology examines both the source and content of incoming messages. By analyzing patterns and suspicious elements, the system effectively filters out potentially dangerous emails before they reach your inbox.
3. URL Protection Through Safe Links
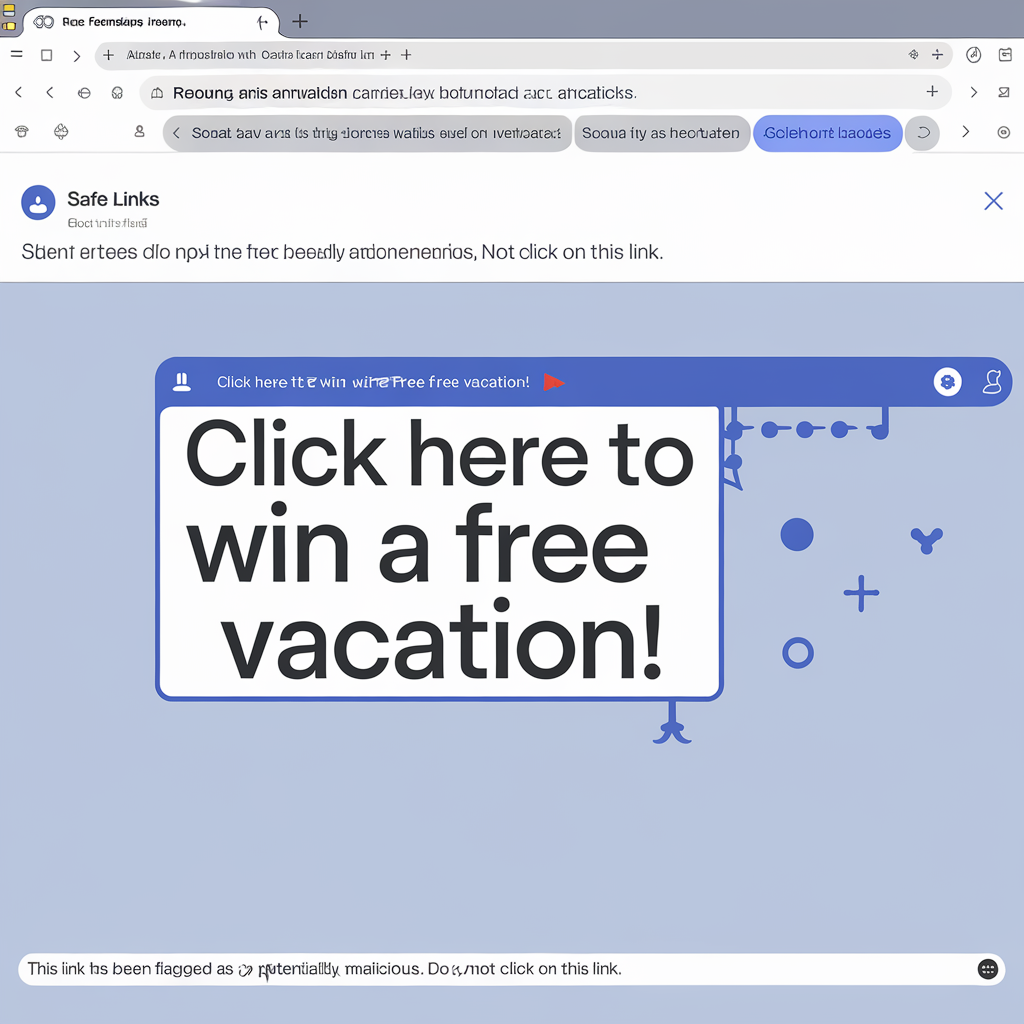
Microsoft 365 Defender phishing protection includes sophisticated URL scanning capabilities that:
- Analyze links in real-time
- Warn users about suspicious websites
- Protect against malware downloads
- Monitor links in SharePoint and Teams
4. Sandbox Isolation
All suspicious attachments are automatically opened in an isolated environment, preventing potential malware from affecting your actual system. This feature provides crucial protection against zero-day attacks and unknown threats.
Implementing Microsoft 365 Defender for Maximum Protection
Best Practices for Deployment
- Regular security audits
- Employee training programs
- Customized security policies
- Continuous monitoring
- Regular updates and maintenance
Configuration Tips for Enhanced Security
To maximize your Microsoft 365 Defender phishing protection:
- Enable Advanced Threat Protection features
- Configure anti-spoofing settings
- Set up safe attachment policies
- Implement safe links policies
- Regular policy reviews and updates
Employee Training and Awareness
Building a Security-Conscious Culture

The most robust technical solutions must be complemented by well-trained employees. Implement regular training sessions focusing on:
- Identifying suspicious emails
- Proper handling of sensitive information
- Reporting procedures for potential threats
- Best practices for password management
- Safe browsing habits
Measuring and Monitoring Security Performance
Key Metrics to Track
- Number of blocked phishing attempts
- Employee reporting rates
- False positive rates
- Response time to threats
- Security policy compliance
The Business Impact of Strong Phishing Protection
Return on Investment
Implementing robust Microsoft 365 Defender phishing protection offers significant benefits:
- Reduced risk of data breaches
- Lower cybersecurity insurance premiums
- Improved customer trust
- Enhanced regulatory compliance
- Protected brand reputation
Future-Proofing Your Security
Staying Ahead of Evolving Threats
As cyber threats continue to evolve, Microsoft 365 Defender constantly updates its protection mechanisms. Regular updates ensure:
- Protection against new threat vectors
- Enhanced detection capabilities
- Improved response mechanisms
- Better integration with existing security tools
Microsoft 365 Defender phishing protection represents a crucial investment in your organization’s cybersecurity infrastructure. By combining advanced technical features with proper implementation and employee training, businesses can significantly reduce their risk of falling victim to phishing attacks and other cyber threats.
Taking Action
To ensure your business remains protected:
- Assess your current security posture
- Implement comprehensive protection measures
- Regular training and updates
- Monitor and adjust security policies
- Stay informed about emerging threats
This comprehensive approach to security, powered by Microsoft 365 Defender’s robust features, provides the protection modern businesses need in an increasingly threatening Internet World.

